Automatic Retries
If the webhook server returns a non-200 response, Flipt will retry sending the request using an exponential backoff strategy until a maximum elapsed duration. The default maximum elapsed duration is 15 seconds. You can configure the maximum duration using the following configuration:Security
You may provide a signing secret for requests to your webhook. If you specify a signing secret, you will receive a request with theX-Flipt-Webhook-Signature header populated. This value can be set in the Audit Events - Webhook section of the Flipt server configuration.
The value in the X-Flipt-Webhook-Signature header is the request body HMAC SHA256 signed with the signing secret you specified. On the webhook server, you can validate the signature by using the same signing secret. It’s strongly recommended that you do this to prevent requests to your webhook server that are from invalid origins.
Templates
Starting from v1.28.0, you can specify a template for the body of an Audit Event Webhook request. A sample configuration can look something like this:POST request when events need to be emitted to the URL https://example.com with the HTTP headers, Content-Type and Authorization, and the body which is a Go template that will be executed when an event comes in. The event structure looks like this:
Example: Slack
Below is an example of a Slack webhook integration that uses the templating feature to send a Slack message when a flag is updated.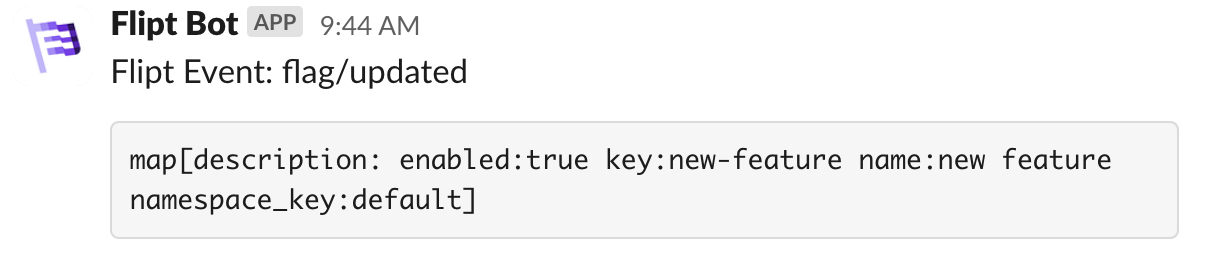 You can find more information about Slack webhooks here. You can also use the Slack Block Kit Builder to build more complex messages.
You can find more information about Slack webhooks here. You can also use the Slack Block Kit Builder to build more complex messages.
